On Thursday, November 29th, 2018, I presented this topic at the National Institute of Standards and Technology (NIST) International Face Performance Conference (IFPC) in Gaithersburg, MD.
“And suddenly, face recognition technology was everywhere…”
Well, we can’t say that yet, but in a few years that is how it will feel.
While government agencies have made effective use of face recognition (FR) technology for over a decade to reduce fraud and enhance public safety, only recently has there been wide adoption by commercial industry. With the exception of Apple’s FaceID and a handful of online services where uploaded selfies are matched against driver’s licenses, most people have yet to interact with FR technology. However, across the world new systems and applications are being developed to streamline and strengthen trust and security of our ever growing global population.
In this article we provide a sneak peak at the different applications coming to market.
Our partners and customers use the ROC SDK to build these applications. As the provider of a quality, native face recognition SDK, we have a front row view of the systems that developers are building.
What is fueling the growth of commercial face recognition applications?
The two biggest enablers in the pending surge in commercial FR systems are a dramatic increase in the accuracy and accessibility of FR algorithms.
In terms of accuracy, the whole face recognition industry has witnessed a revolution in the past few years due to the emergence of deep learning frameworks and convolutional neural networks. Rank One is one of several algorithm providers on the forefront of this innovation, and here is a snapshot of how our accuracy has improved in the last two years on challenging unconstrained imagery.
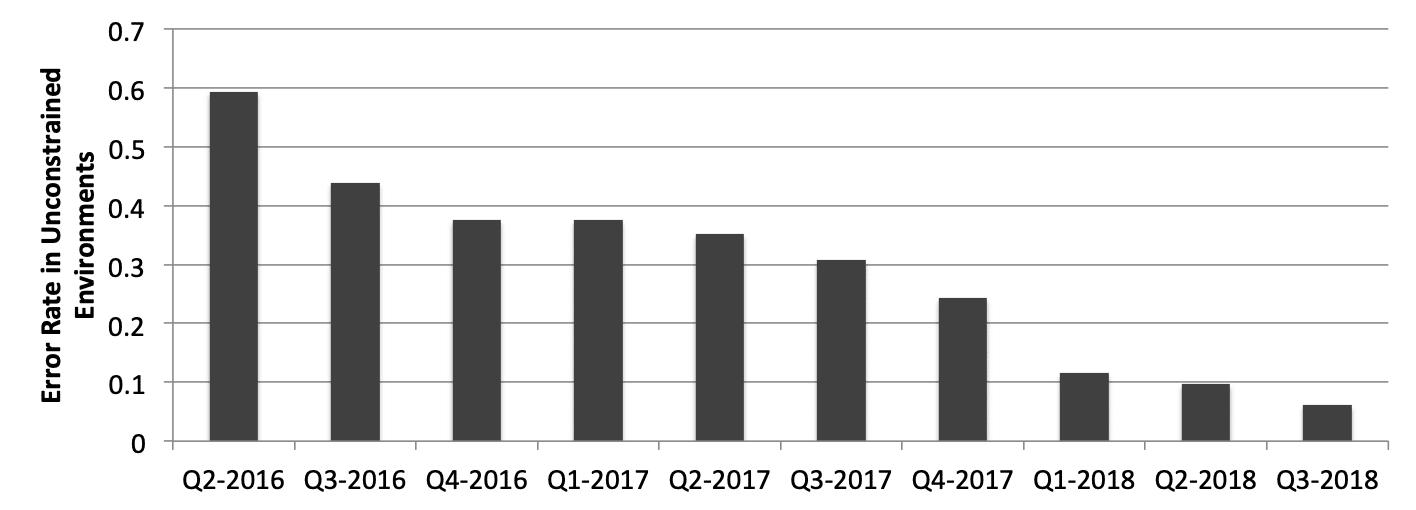
Over a 10x reduction in error rate has been achieved by the ROC SDK over the past two years on challenging unconstrained facial imagery. This improvement is similar to many of the top performing algorithms in the industry, which is enabling new commercial applications.
In the above plot, error rate is defined as the identity verification False Rejection Rate at a fixed False Acceptance Rate of 1 in 10,000.
In terms of improved accessibility, this applies in two different respects. For one, many algorithms are faster than ever, and are able to run directly on mobile devices and low cost hardware. Second, the licensing cost for algorithms has fallen due to more available solutions in the marketplace.
So, what are these emerging applications in commercial industry?
Identity Proofing
As the world’s economies steadily shift from brick-and-mortar businesses to digital platforms, and as regulatory requirements to “Know Your Customer” (KYC) increase accordingly, the “Identity (ID) Proofing” industry comes to the rescue.
An ID Proofing solution receives as input a photograph of an ID card (e.g., a driver’s license) and a selfie, typically captured through a mobile app (e.g., for a bank or an online marketplace). The ID Proofing software in turn validates the authenticity of the ID card through numerous checks to ensure it is a valid, un-tampered, and un-expired document. Additionally, the photograph in the ID card is cropped and compared against a user-submitted selfie photo using a face recognition engine to determine if they are a match. Finally, various measures are performed to ensure the selfie is a live presentation and not a replay attack (i.e., the person in the selfie was physically present).
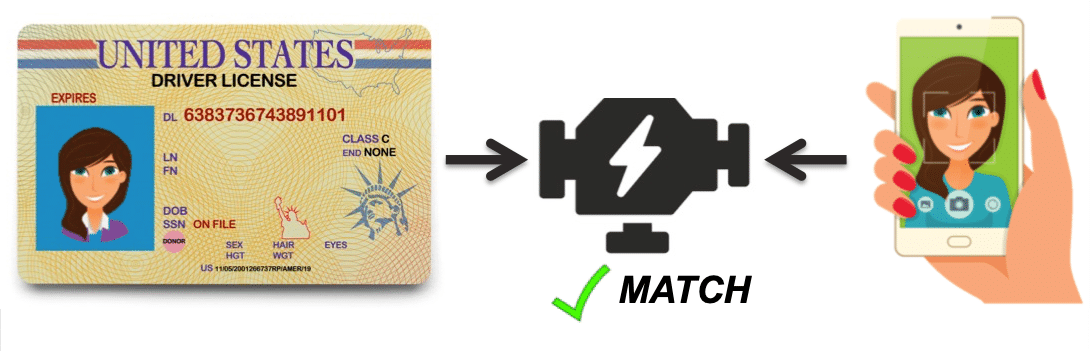
ID Proofing systems compare the image in an ID card to a selfie image to validate a person’s identity.
Most ID Proofers do not develop their own face recognition algorithm. It is enough work already to build robust ID validation software compliant with security requirements for the financial industry and large enterprises. Instead, ID Proofers can easily integrate a third-party face recognition SDK to cover this piece of the puzzle.
ID Proofing systems typically have the following requirements in a recognition SDK:
- Highly accurate on “selfie” images, which are characterized by:
- Pitch variations
- Inconsistent illumination
- Lens distortion
- Highly accurate on scanned ID card photos, which are characterized by:
- Holograms
- Printer artifacts
- Low-resolution
- Time lapse
- Robust anti-spoof (liveness validation) using generic sensors (e.g., front facing cameras)
Real-time screening
Whether it is in airports, stadiums, or other critical infrastructure, a tremendous amount of human labor is spent screening persons passing through various checkpoints. This process is both costly, and error prone as humans are not very good at performing “unfamiliar” face recognition, and the other-race effect is generally more prominent in humans than machines.
As the accuracy and speed of automated algorithms continue to improve, it is increasingly realistic to automatically identify persons passing through controlled checkpoints. These systems are intended to be run by security officials, with alerts typically examined by a human operator. Focusing human operators on only the exceptional identification cases reduces examiner fatigue and increases checkpoint throughput.
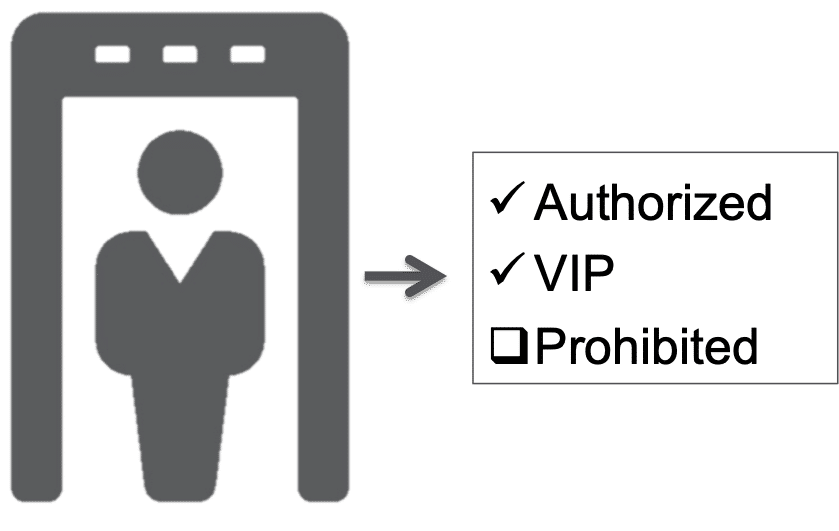
Real-time screening systems can validate a person’s identity against provided credentials (e.g., employee badge, ID card, or an event ticket), and/or compare them to alert lists (e.g., VIP’s, or prohibited persons).
Real-time screening systems have the following requirements:
- Accurate in semi-unconstrained and semi-cooperative settings:
- Faces that are near-frontal
- Lighting is semi-controlled
- The ability to run on low-cost processors (e.g., ARM):
- ARM processors are an order-of-magnitude less cost than x86/x64 processors. Algorithms that are efficient enough to run on low cost processors can save significant costs in the development of real-time screening systems.
- The ability to run on low cost cameras:
- Cameras suitable for this application can range in cost from $100 to over $1,000. Algorithms that are tolerant to lower resolution imagery can thus save significant camera costs.
- Ease of integration and use:
- Typically only a native SDK is considered for these applications as it is too slow and error prone to send acquired imagery over a network to a cloud-based API.
- A simple face recognition API can save in software development costs by reducing the amount of engineering effort required to develop and maintain the solution.
Access control
Authentication systems increasingly rely on biometrics, whether this is in a single-factor or multi-factor authentication system. Face recognition has become particularly appealing for access control given its contactless nature.
The most common access control application for face recognition is mobile device unlock, which became quite prominent when Apple released the FaceID system in the Fall of 2017. Since then a number of different technology providers have been working to deliver similar solutions to the Android market.
Other common access control applications for face recognition are time-and-attendance and facility access systems. These systems are generally “unattended” in that there is no human operator, and users present their face along with any additional authentication factors, and are provided access to a facility or are clocked in and out accordingly.
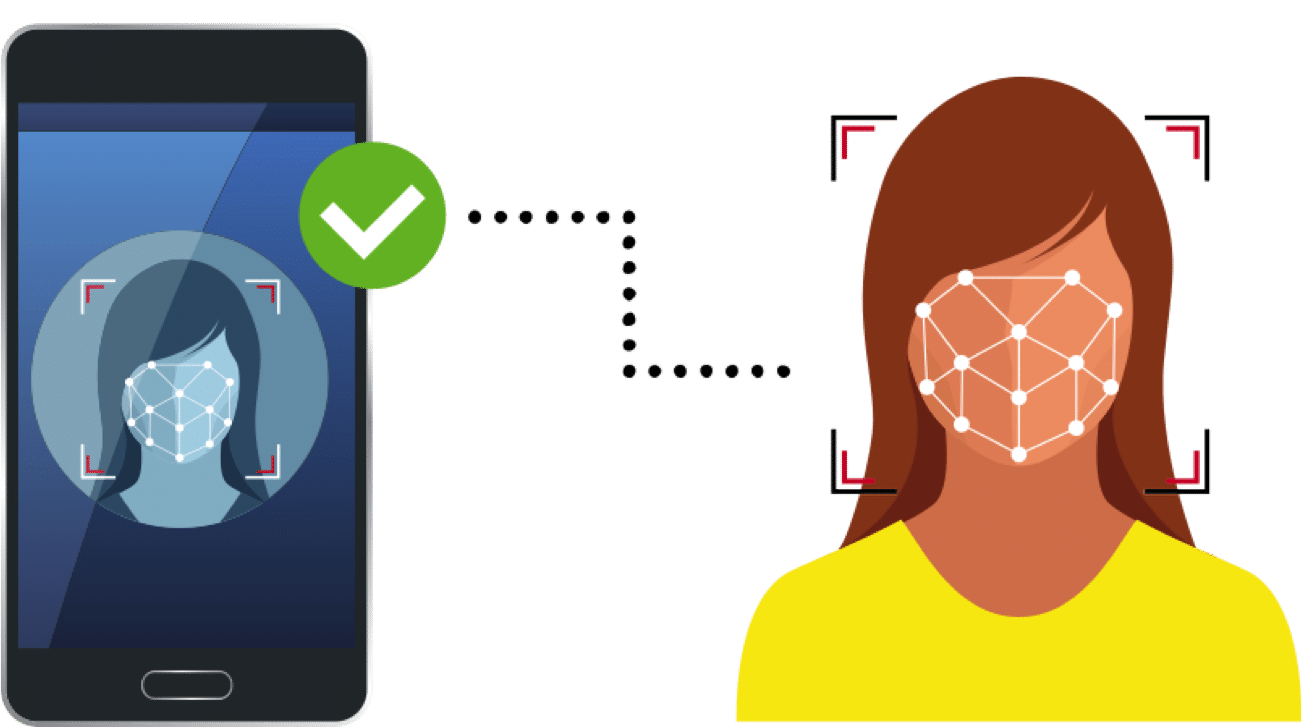
Access control systems will grant access to a system or facility when a presented face matches the claimed identity.
Key requirements include:
- Accuracy on selfie-style images
- The ability to run on low cost processors (e.g., ARM)
- Extreme power efficiency:
- Access control on mobile phones means battery powered processors. Thus, the fewer computational instructions required for enrollment and matching the less power consumed.
- Minimal binary footprint (RAM):
- The models and libraries required by the FR algorithm need to be loaded into RAM to enable rapid authentication. In the case of mobile phones, this RAM usage cannot be significant or other applications will suffer.
- Robust anti-spoof:
- Access control systems are fully automated, and need methods to distinguish between a physically present person and a replay attack from a digital screen or printed photo.
Slower Emerging Applications
There are other commercial applications that have not yet crossed the chasm. Several technology startups and stalwarts are quietly incubating the following FR applications:
Internet of Things (IoT)
Whether it is our car, our thermostat, our doorbell, or our refrigerator, the next generation of applications and vehicles will be fully interconnected, will know when we are present, and will adapt accordingly.
Requirements:
- Strong accuracy in unconstrained settings
- Support for low cost hardware (e.g., ARM)
Smart Retail
Retailers want to know who is buying what products, both at the individual level (e.g., Brendan loves Homer Simpson socks), and across demographic cohorts (e.g., men aged 35 to 50 always buy product X). Customers often want rewards. And, payment providers want reduced fraud. Smart retail systems powered by FR technology can enable all of these advancements.
Requirements:
- Strong accuracy in unconstrained settings
- Affordable software licensing fees
Medical Patient Identification
Enhanced patient identification reduces insurance fraud and can help streamline the delivery of medical services.
Requirements:
- Ability to run on mobile devices (e.g., tablets carried by doctors)
- Ability to run on low cost hardware (e.g., kiosks at medical care check-in and pharmacies)
Summary
Face recognition technology is no longer limited to the role of keeping our communities safe through the various government and law enforcement applications that have been in place for over a decade. It is rapidly expanding as a convenience technology that allows quick and secure access to sensitive systems and facilities, and for people to ubiquitously interact with their environments. This article highlighted the most prominent emerging commercial applications of face recognition technology.