There is a misconception that law enforcement agencies in the U.S. use automated face recognition to actively surveil public spaces. Such a dragnet of mass real-time identification and surveillance would be a violation of the Fourth Amendment to the United States Constitution. While autocratic countries may intend to use face recognition technology for nefarious purposes, in the United States, and other nations with inalienable human rights, there is no systematic intent or process designed to exploit facial recognition technology in this manner.
Concerns that face recognition could be used to invade privacy are valid; however, this is not how it is being used by U.S. law enforcement. To the contrary, law enforcement primarily uses face recognition as a post-incident forensic tool to enable detectives and analysts to generate investigative leads in violent and harmful crimes.
In this article we explain both how forensic face recognition works, and how it is used by law enforcement in this country.
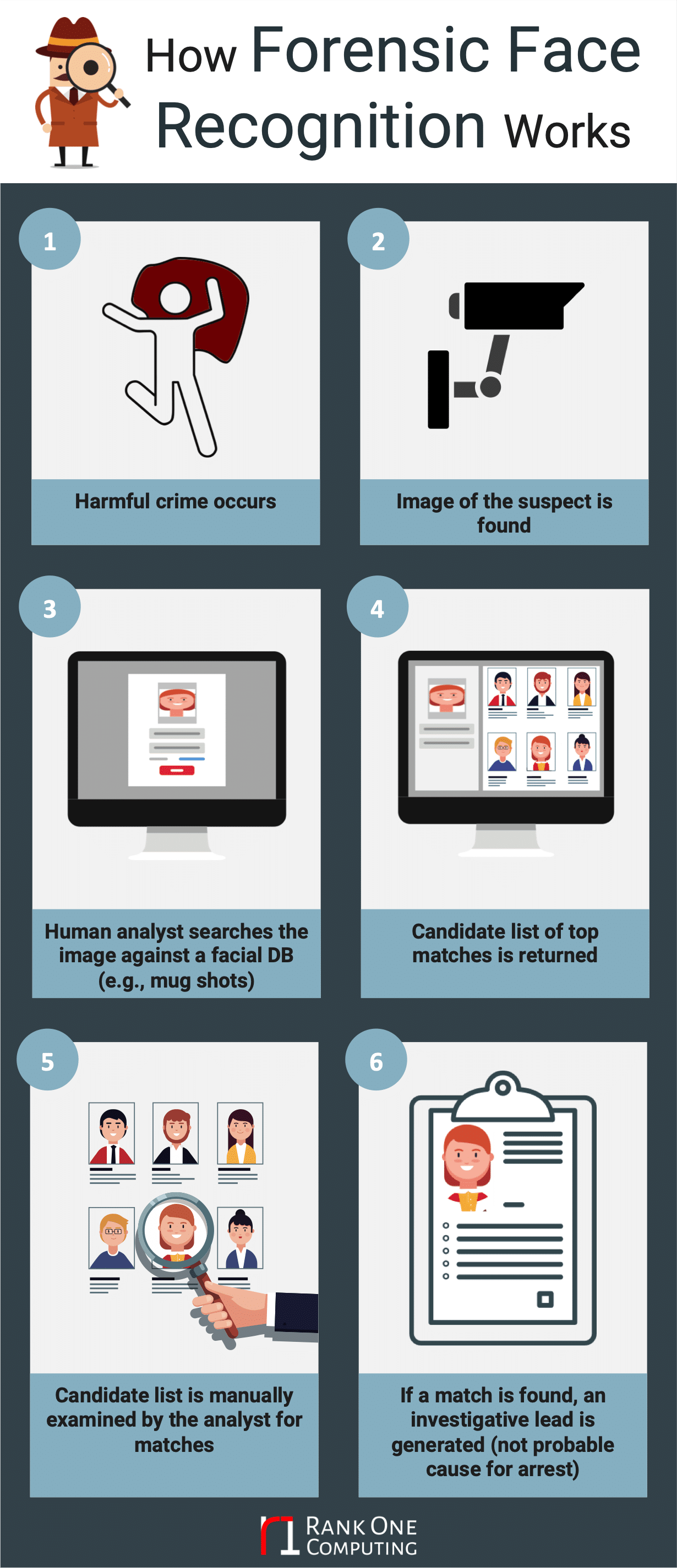
Step 1: A violent or harmful crime occurs
While modern societies have become safer with each passing decade, there were still over a million incidents of violent crime in the U.S. in 2017. These incidents range from murder (17,284 incidents), to rape (135,755 incidents), to aggravated assault (810,825 incidents), amongst many other crimes. Similarly, cases of burglary, larceny, arson, and fraud take a tremendous toll on victims.
Step 2: An image of a perpetrator (or victim) is available.
This image of the perpetrator could come from a number of different sources. For example:
- The victim of a sexual assault could have the perpetrator’s image from an online dating site they met on.
- A store owner who was the victim of an armed robbery could have a camera system installed that captured the robber’s face.
- A high density tourist area may have recorded footage of a terrorist leaving a bomb.
- A video of an unidentified adult engaging in inappropriate acts with a child may emerge while a warrant is being served for a related crime.
- A homeowner’s doorbell may capture a picture of a burglar.
- A traffic camera may have captured a person’s face before a violent act of road-rage.
In certain cases it is instead a victim who needs to be identified. This could be a deceased person without identification, or a victim filmed in a child exploitation case.
Step 3: An investigator or analyst searches the image against a database
The photograph or video frame image of the unidentified person of interest, often referred to as a probe image, is sent to a detective, analyst, or operator who manages digital forensic evidence. This human operator in turn uses automated face recognition to search the probe image against an available database of face images (often referred to as the gallery).
The galleries that are available for this search-and-compare process will vary, depending on the agency and jurisdiction. For most law enforcement agencies this will include mugshot arrest images. For certain law enforcement agencies, depending on state and local laws, the database may also include images from other Government agencies that grant identification cards (e.g., DMVs), criminal watch lists, or data otherwise meaningful to share.
Step 4: A candidate list is returned that contains the closest matching faces
Once this automated search is complete, the operator of the system will receive back a rank-ordered list of the top matches, where the first result is the image in the gallery that has the highest similarity score to the probe image. The second result will be the image in the gallery second highest similarity score, and so on.
The number of candidate matches returned will vary depending on the configuration of the system. For example, in some configurations only images that exceed a certain similarity score are presented. In other systems, the top N results are returned, regardless of similarity score, where N may be 20, 50, or 100.
Step 5: Candidate list is examined by the analyst
The operator of the system, who has often been trained in facial comparison, will examine the returned candidate list to determine if any of the candidate images match the person of interest in the probe image.
When performing comparisons, the analyst will examine the various morphological features of the face and document the entire comparison process. Most forensic search systems have automated tools that significantly improve an analyst’s ability to compare the two faces and document the process.
Step 6: If the analyst determines there is a high likelihood of a match, then an investigative lead report is generated
If the probe image from the person of interest has facial characteristics that indicate a strong match to a person in the gallery, then an investigative lead report is generated.
An investigative lead is not probable cause for arrest. The detective investigating the crime will use the investigative lead generated from face recognition technology as a potential clue; a clue that could potentially lead to solving the case.
Public safety benefits, without harm
An investigative lead generated by the forensic face recognition process could be the difference between whether or not a person who inflicts harm upon others is identified. This investigative method has tremendous benefits in terms of public safety. When performed under proper standards, this forensic procedure does not have the propensity for harm mistakenly claimed by those who think this use is akin to active real-time surveillance.
Given the percolating misunderstanding of how law enforcement agencies use automated face recognition technology, we will summarize certain points covered in this article as they relate to myths around use of the technology in the U.S.:
- There is not a mass network of cameras that are identifying persons in real-time across public spaces.
- Automated face recognition in law enforcement is predominantly a post-incident method used when a harmful crime occurs, and is a key forensic crime-solving tool
- The results from an automated face recognition search are carefully examined by an analyst or operator. If an analyst finds a strong likelihood of a match, this information is considered an investigative lead, and is not probable cause for arrest.
- There are no documented cases in the U.S. of invasion of privacy or wrongful arrest due to forensic face recognition despite over a decade of successful use.
Governing the use of face recognition technology is a good idea, but it must come from an informed point of view. When legislators make decisions based on campaigns of misinformation, the safety of their constituents suffers. Face recognition technology, used as a forensic process, provides incredible benefits that greatly enhance the safety of our citizens without compromising guaranteed civil liberties or privacy rights.
–
Like this article? Subscribe to our blog or follow us on LinkedIn or Twitter to stay up to date on future articles.
Popular articles:
- How Automated Face Recognition Works
- Emerging Trends in Commercial Face Recognition
- 10 Steps for Selecting a Face Recognition Algorithm